We first met Edward Farrell from Mercury ISS at CyberCon 2019. He’s since become one of HackHunter’s valued advisors, testing every version of the Pursuit tracker and giving us valuable feedback on how it would be used in the field. He took the latest Pursuit with him to DEF CON and found “that the HackHunter was able to operate effectively in one of the most publicly hostile environments”. Here’s Edward’s experience:
TL:DR – A rogue access point was detected and hunted down using the HackHunter Pursuit at DEF CON in a room of 400 to 500 people in only 6 minutes!
DEF CON was a bit of a surreal one this year for me. It’s been about 3 years since being able to attend in person and I wasn’t going to miss the first opportunity to get back into the event. In addition to the renowned socialising, the event’s education, talks and radical approach to education are phenomenal. I always leave feeling a little more humbled and inspired to do better. It is also reasonable to say that from a cyber security standpoint, everything is fair game (within a limit) and the entertainment of social interaction, discovery and even circumventing cybersecurity controls in a safe environment make this one of the best training grounds in the world.
During the event I decided to make use of the HackHunter device I’ve been contributing to and using as part of work. Some of my existing 802.11 work in direction-finding devices has been a bit ad-hoc and a challenge, investing time, money and effort into supporting the product has been rewarding. During the event I wanted to assess the rogue access point detection features I’d been contributing to, and thankfully on Saturday afternoon at 3:54pm someone was kind enough to appear on the radar. Before I dive further into this piece, it’s important to note that at DEF CON, if you are connecting to WiFi or have devices with a WiFi interface turned on, it is going to get picked up and will be fair game; this is not a good or bad thing, it’s simply a reality of DEF CON. The rogue access point was immediately flagged within HackHunter based on some common traits that I’ve observed in PCAPS and other parameters that meant the device “went orange” on the HackHunter and warranted a detailed hunt. I was in the contest area, illustrated below:
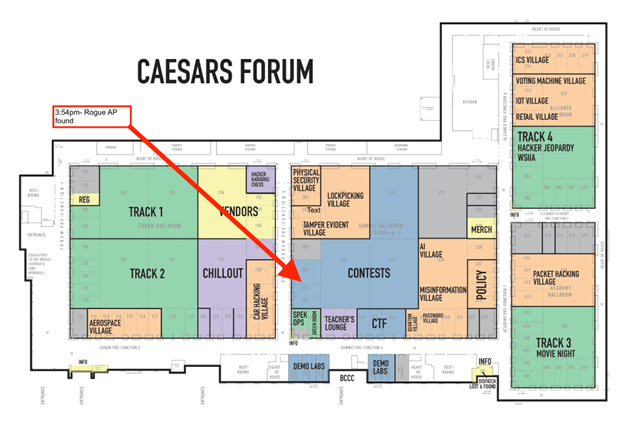
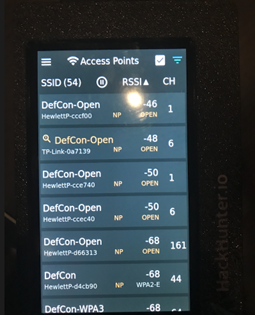
The contest area space where the rogue access point was likely located was approximately 250 square meters and had at least 400 to 500 people inside, as well as several tables, access points and other wirelessly enabled competitions. Using the HackHunter and locked onto the target mac address, I systematically went through the environment which was constantly moving until I dialled right in on the rogue access point which had an antenna sticking out of the bag- a slightly obvious marker. Having identified the device at 4:01, the process of hunting took about 6 minutes: this is substantially faster than previous attempts at DEF CON, where it would take 20 minutes, by which time the rogue AP had already departed the environment. The setup on the pack (illustrated below) was pretty awesome and in conversation with the owner was fairly benign. Having high fived the owner on a cool setup and taken a photo with permission, I went on my way.

Following this activity and a general discussion with colleagues, a few things became apparent:
- Anyone who was set to automatically connect to the DefCon-Open network would have inadvertently connected to the network in the environment outside the main auditorium. Also, as it was the strongest signal in the contest area, these devices may have jumped onto the network. I didn’t check with the owner how many connections took place.
- The intent of the person with the pack was to see who was connecting to what and identify DNS records. Their actions were fairly benign and the intent of seeing who connected and outputs from this connection without full MITM was fairly benign. Far worse could be achieved through say injection of code based on requests or even active scanning.
One of the things this tested for me was that we were able to move fast. Cyber security is a game of maneuver warfare; being able to move at speed would ensure a fast termination and denying freedom of movement. Previous iterations of such activities have also seen threat actors depart before being found, so the speed of discovery was also an epic attribute. The fact that the HackHunter was able to operate effectively in one of the most publicly hostile environments I think is a testament to its capability.



